If a domain controller that holds one or more of the five FSMO roles becomes permanently unavailable, you’ll ultimately need to seize the roles to another domain controller. Seizing FSMO roles is not a graceful process and is intended only to be performed when the unexpected occurs. In normal day-to-day operations, if you need to change what domain controller a FSMO role is held by, you should instead transfer the role. In order to seize the RID Master, PDC Emulator, or Infrastructure Master, you’ll need to be logged in as a Domain Admin. To seize the Schema Master or Domain Naming Master, you must be logged in with Schema Admin or Enterprise Admin permissions, respectively.
In this example, we’ll seize the PDC Emulator to a domain controller called coho-chi-adc02. I have provided the commands to seize each of the four other FSMO roles at the conclusion of these steps.
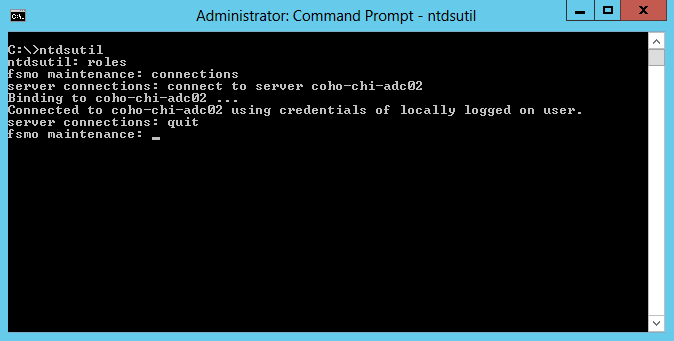
- Open an elevated command prompt
- Type ntdsutil and press Enter.
- Type roles and press Enter.
- Type connections and press Enter.
- Type connect to server coho-chi-adc02 and press Enter.
- Type quit and press Enter. Your screen should look similar to the following after this step:
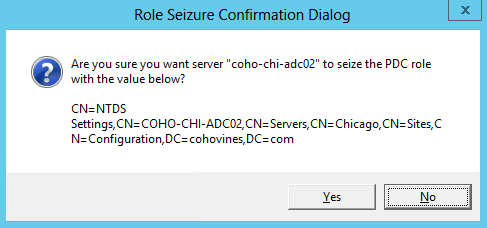
- Type Seize PDC and press Enter. You will be prompted to confirm the seizure as shown below. Once you click yes, the seizure process will begin. This will take some time to complete. As a safety mechanism, NTDSUtil will first try to transfer the role. This should timeout and fail and then the actual seizure will occur.
Once the seizure occurs, you will see output similar to the following written to the console. While the output includes an error, the important success message (highlighted in yellow) is also included.
Attempting safe transfer of PDC FSMO before seizure.
ldap_modify_sW error 0x34(52 (Unavailable).
Ldap extended error message is 000020AF: SvcErr: DSID-032105B1, problem 5002 (UNAVAILABLE), data 1722Win32 error returned is 0x20af(The requested FSMO operation failed. The current FSMO holder could not be contacted.)
)
Depending on the error code this may indicate a connection,
ldap, or role transfer error.
Transfer of PDC FSMO failed, proceeding with seizure ...Server "coho-chi-adc02" knows about 5 roles
Schema - CN=NTDS Settings,CN=COHO-CHI-ADC01,CN=Servers,CN=Chicago,CN=Sites,CN=Configuration,DC=cohovines,DC=com
Naming Master - CN=NTDS Settings,CN=COHO-CHI-ADC01,CN=Servers,CN=Chicago,CN=Sites,CN=Configuration,DC=cohovines,DC=com
PDC - CN=NTDS Settings,CN=COHO-CHI-ADC02,CN=Servers,CN=Chicago,CN=Sites,CN=Configuration,DC=cohovines,DC=com
RID - CN=NTDS Settings,CN=COHO-CHI-ADC01,CN=Servers,CN=Chicago,CN=Sites,CN=Configuration,DC=cohovines,DC=com
Infrastructure - CN=NTDS Settings,CN=COHO-CHI-ADC01,CN=Servers,CN=Chicago,CN=Sites,CN=Configuration,DC=cohovines,DC=com
To seize the other roles, run the following commands in lieu of “Seize PDC”. If you are seizing multiple roles, you can seize them sequentially without repeating steps one through six:
- Domain Naming Master – “Seize naming master”
- Infrastructure Master – “Seize infrastructure master”
- RID Master – “Seize RID master”
- Schema Master – “Seize schema master”
Once you have completed seizing the roles you need, you can close the command prompt. The changes will replicate throughout your forest via normal channels.