Delegating Enable/Disable Account Rights in Active Directory
A common question is "How do I delegate enabling and disabling Active Directory accounts?". Unfortunately, these specific operations cannot be individually delegated. The flag that indicates whether a user is enabled or disabled is part of a bitmask called userAccountControl. The vast majority of options in this bitmask are the checkboxes that you see on the account tab of ADUC:
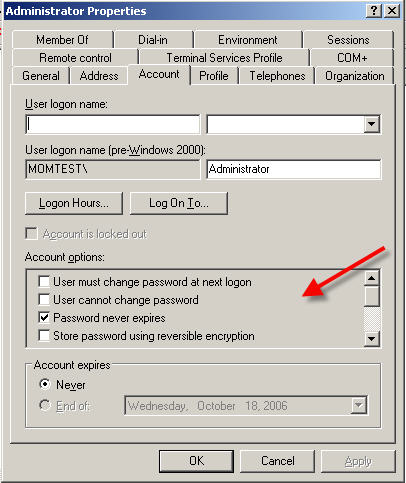
The complete list of what's stored in the bitmask (copied out of the iads.h header) is below. Most of them should be fairly self explanatory but this MSDN article explains them all. The numbers are the bit which represents this value in the mask (in hex):
- ADS_UF_SCRIPT = 0x1
- ADS_UF_ACCOUNTDISABLE = 0x2
- ADS_UF_HOMEDIR_REQUIRED = 0x8
- ADS_UF_LOCKOUT = 0x10
- ADS_UF_PASSWD_NOTREQD = 0x20
- ADS_UF_PASSWD_CANT_CHANGE = 0x40
- ADS_UF_ENCRYPTED_TEXT_PASSWORD_ALLOWED = 0x80
- ADS_UF_TEMP_DUPLICATE_ACCOUNT = 0x100
- ADS_UF_NORMAL_ACCOUNT = 0x200
- ADS_UF_INTERDOMAIN_TRUST_ACCOUNT = 0x800
- ADS_UF_WORKSTATION_TRUST_ACCOUNT = 0x1000
- ADS_UF_SER…